It’s been a while since I’ve blogged about anything so it’s only fitting that I post about doing something fairly trivial. I say it’s trivial because Fiddler makes my job so gosh-darn easy!
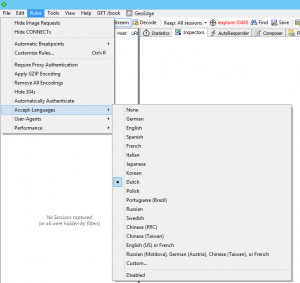
I often find myself testing that web sites work in various other languages. In many cases, changing the Accept-Language for a site will do the trick and luckily Fiddler’s custom rules will let you do the trick. The software allows you to specify Japanese as an option under the Rules menu.
That said, simply testing one language isn’t usually enough. I’d find myself hitting CTRL+R to open the CustomRules.js file, editing the Accept-Language and waiting for another day before I’d need to do this again.
I got tired of this today and completely removed the single-instance Japanese support option from Fiddler. So I replaced this code:
// Cause Fiddler to override the Accept-Language header
public static RulesOption("Request &Japanese Content")
var m_Japanese: boolean = false;
With this code:
// Cause Fiddler to override the User-Agent header with one of the defined values
RulesString("&Accept-Languages", true)
BindPref("fiddlerscript.ephemeral.AcceptLanguage")
RulesStringValue(0,"None", "")
RulesStringValue(1,"German", "de")
RulesStringValue(2,"English", "en")
RulesStringValue(3,"Spanish", "es")
RulesStringValue(4,"French", "fr")
RulesStringValue(5,"Italian", "it")
RulesStringValue(6,"Japanese", "ja")
RulesStringValue(7,"Korean", "ko")
RulesStringValue(8,"Dutch ", "nl")
RulesStringValue(9,"Polish", "pl")
RulesStringValue(10,"Portuguese (Brazil)", "pt-br")
RulesStringValue(11,"Russian", "ru")
RulesStringValue(12,"Swedish ", "sv")
RulesStringValue(13,"Chinese (PRC)", "zh-cn")
RulesStringValue(14,"Chinese (Taiwan)", "zh-tw")
RulesStringValue(15,"en-us, fr-fr", "en-us, fr-fr")
RulesStringValue(16,"ru-mo, de-at, zh-tw, fr", "ru-mo;q=1,de-at;q=0.9,zh-tw;q=0.8,fr;q=0.6")
RulesStringValue(17,"&Custom...", "%CUSTOM%")
public static var sAL: String = null;
And later in the file, I replaced this code:
if (m_Japanese) {
oSession.oRequest["Accept-Language"] = "ja";
}
with this code:
// Accept-Language Overrides
if (null != sAL) {
oSession.oRequest["Accept-Language"] = sAL;
}
Now every time I open Fiddler, I can just select the language I want to use.